Computer security protects digital information from threats. It keeps data safe from unauthorized access.
As technology advances, security becomes more crucial. Understanding computer security helps protect personal and professional information. Various types exist, each with unique features and purposes. These security measures guard against hackers, viruses, and data breaches. With cyber threats growing daily, knowing different security types is vital.
It helps you choose the right protection for your needs. Some types focus on data encryption, while others on network safety. Each serves a specific role in safeguarding information. Proper security ensures privacy, integrity, and availability. Learn about these security types to keep your digital world secure.
Introduction To Computer Security
Computer security is essential in today’s digital world. It safeguards our data, privacy, and online transactions. With technology evolving, cyber threats are becoming sophisticated. Learning about computer security types is crucial.
Importance Of Security
Security protects sensitive data from unauthorized access. It ensures privacy and builds trust in digital interactions. Businesses rely on security to protect customer information. Individuals need it to secure personal data and communications.
Evolution Of Threats
Cyber threats have changed significantly over time. In early computing, viruses were the primary threat. Now, threats include ransomware, phishing, and DDoS attacks. Hackers find new ways to bypass security measures. Understanding threat evolution helps in creating better defenses.
Network Security
Network security protects data and resources from cyber threats. It ensures safe communication over networks. This area of computer security is crucial for businesses and individuals. Effective network security measures prevent unauthorized access. They also protect against data breaches and cyberattacks.
Firewalls And Their Role
Firewalls act as barriers between networks. They control the flow of data. Firewalls filter incoming and outgoing traffic. They block harmful or suspicious data packets. This helps prevent unauthorized access to networks. Firewalls can be hardware or software-based. They are essential for any secure network setup.
Firewalls are like security guards for your network. They monitor and decide what enters or exits. This keeps your data safe from external threats.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) identify unauthorized activities. They monitor network traffic for suspicious behavior. IDS alert administrators of potential threats. They analyze data to detect anomalies and attacks. An IDS helps in early threat detection. This allows quick response to breaches.
IDS are crucial for maintaining network integrity. They provide an extra layer of security. By detecting threats early, IDS safeguard sensitive information.
Application Security
Application security protects software from threats. It focuses on safeguarding apps during development and deployment. Essential in computer security, it prevents unauthorized access and data breaches.
Application security is a crucial part of protecting your digital environment. It focuses on safeguarding software applications from threats and vulnerabilities that could lead to data breaches or system compromises. Whether you’re using a mobile app, web service, or desktop software, application security ensures that these tools function safely and reliably.Securing Software Applications
Securing software applications involves multiple strategies to keep them safe. You might think of it as putting locks on every door and window of your digital house.Developers use practices like code reviews and penetration testing to spot weaknesses. Regular updates and patches are essential to fix bugs that could be exploited by attackers.Have you ever noticed an app update on your phone and wondered why it’s so frequent? These updates often contain security patches that protect against new threats.Common Vulnerabilities
Understanding common vulnerabilities helps you better protect your applications. One frequent issue is SQL injection, where attackers manipulate a database through an application.Another is cross-site scripting (XSS), where malicious scripts are injected into trusted websites. Both can lead to data theft or unauthorized access.Imagine if a simple click on a link could expose your personal information. It’s vital to be aware of these vulnerabilities to prevent such scenarios.By staying informed and proactive, you can enhance the security of your applications and protect your data. What steps can you take today to ensure the apps you use are secure?Endpoint Security
In the realm of computer security, endpoint security stands crucial. It safeguards devices like laptops and smartphones from cyber threats. As cyberattacks grow, endpoint security becomes essential for protecting data. Businesses and individuals rely on strong endpoint security to keep information safe.
Antivirus Solutions
Antivirus solutions are fundamental in endpoint security. They scan devices for malicious software, removing threats before they cause harm. Regular updates ensure antivirus software can tackle new viruses. Users must choose antivirus solutions wisely for effective protection. Free and paid options offer varying levels of security.
Endpoint Detection And Response
Endpoint Detection and Response (EDR) is a sophisticated security measure. EDR monitors device activity to detect suspicious behavior. It provides real-time alerts for potential threats. EDR solutions allow quick responses to security incidents, minimizing damage. Businesses benefit from EDR by preventing data breaches and maintaining trust.
Data Security
Data security protects your digital information from unauthorized access and corruption. It involves safeguarding sensitive data from breaches and ensuring its integrity. With the rise of cyber threats, data security is crucial for individuals and businesses. Let’s explore two essential aspects of data security: encryption techniques and data loss prevention.
Encryption Techniques
Encryption techniques are methods to protect data by converting it into code. This code is unreadable without a decryption key. Encryption is vital for keeping your data safe from hackers. It ensures that sensitive information remains confidential. Common encryption methods include AES, RSA, and DES. Each of these offers different levels of security. AES is widely used for its strong encryption strength. RSA is preferred for encrypting internet data. DES, though older, is still used in some legacy systems.
Data Loss Prevention
Data loss prevention (DLP) strategies protect information from being lost or stolen. They help in identifying and preventing data breaches. DLP tools monitor and control data transfer across networks. These tools can block unauthorized sharing of sensitive information. They also alert administrators about potential threats. Effective DLP solutions prevent accidental data leaks. They ensure compliance with data protection regulations. Regular data backups also play a crucial role in data loss prevention. Backups help recover data in case of accidental deletion or cyber-attacks.

Credit: www.fynd.academy
Identity And Access Management
Identity and Access Management (IAM) is crucial for computer security. It ensures that only authorized users can access certain resources. IAM helps prevent unauthorized access and protects sensitive data. This system is vital for maintaining security within any organization.
User Authentication Methods
Authentication methods verify the identity of users. Passwords are a common method, but they are not always secure. Two-factor authentication adds an extra layer of security. Biometrics use physical traits like fingerprints for secure access. These methods help ensure that users are who they claim to be.
Role-based Access Control
Role-Based Access Control (RBAC) assigns permissions based on user roles. Different roles have different access levels. For instance, managers may access sensitive data, while employees have limited access. RBAC helps streamline access by defining roles clearly. It reduces the risk of unauthorized access by controlling permissions effectively.
Cloud Security
Cloud security protects data stored online from theft and attacks. It involves encryption, access control, and regular monitoring. This type of computer security ensures safe and private online data storage.
When you think about cloud security, imagine having your most prized possessions stored somewhere outside your home. You need to trust that they’re safe, but how can you be sure? Cloud security is all about protecting your data when it’s stored online. With the rise of cloud services, knowing how to keep your information secure is more crucial than ever. Let’s dive into what makes cloud security essential and how you can ensure your data is safe.Securing Cloud Services
Securing cloud services involves a mix of strategies and tools to protect your data. Start by choosing a reliable cloud service provider with a strong security track record. Many companies offer encryption, which scrambles your data so only authorized users can read it.Additionally, always enable multi-factor authentication (MFA) for accessing your cloud accounts. MFA requires users to provide two or more verification factors to gain access. It’s like needing both a key and a password to open a door. This extra layer of security makes it much harder for unauthorized users to access your information.Challenges In Cloud Security
Despite its benefits, cloud security comes with its own set of challenges. One major issue is data breaches, where unauthorized users gain access to sensitive information. To minimize this risk, regularly update your security settings and review who has access to your data.Another challenge is compliance with data protection regulations. Different countries have different rules about how data should be handled and stored. Make sure you’re familiar with these regulations to avoid legal issues.A personal story here: I once ignored a software update notification for my cloud storage, thinking it wasn’t urgent. A few weeks later, I learned that the update fixed a security vulnerability. It was a wake-up call to always keep my software up-to-date. Are you regularly updating your software to patch security holes?Remember, staying informed and proactive can make a big difference in protecting your data in the cloud. What steps will you take today to secure your cloud services?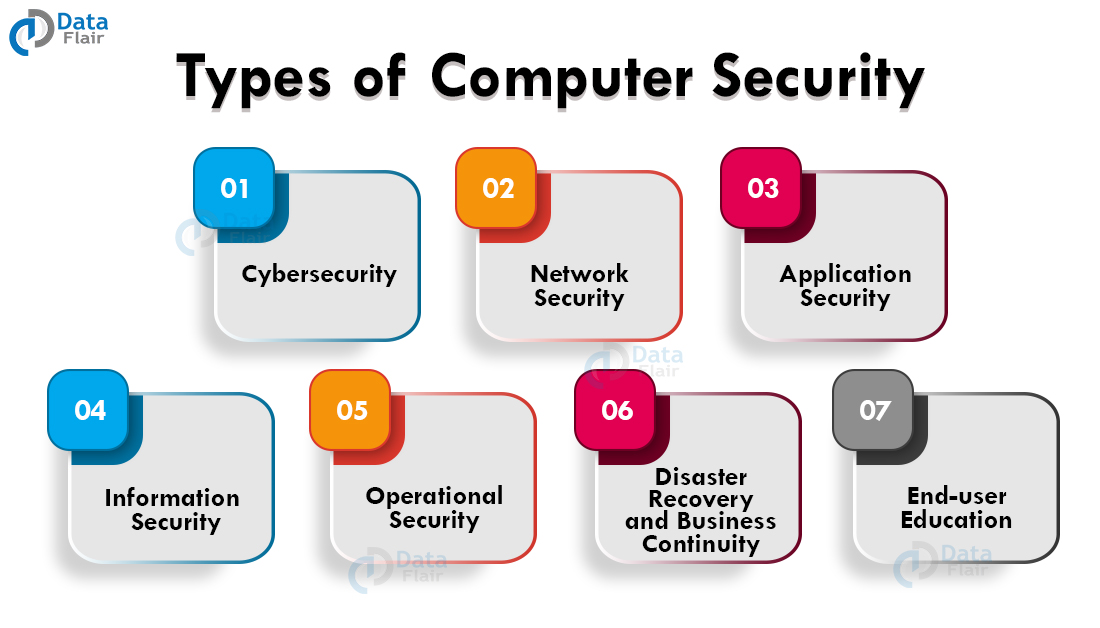
Credit: data-flair.training
Emerging Security Technologies
In the fast-changing world of technology, security methods are also evolving. Emerging security technologies play a key role in protecting digital information. These technologies offer new ways to defend against cyber threats. They enhance traditional methods and bring innovative solutions to the table.
Artificial Intelligence In Security
Artificial Intelligence (AI) is changing how we approach security. AI helps in detecting threats quickly and accurately. It learns from past incidents to predict future attacks. AI automates many security tasks, saving time and resources. It can also analyze large volumes of data efficiently. This makes it a valuable tool in preventing cyber attacks.
Blockchain For Security
Blockchain technology provides a new level of security. It ensures data integrity and transparency. Each transaction in a blockchain is encrypted and linked to the previous one. This makes data tampering difficult. Blockchain is decentralized, reducing the risk of a single point of failure. It is widely used in securing financial transactions and digital identities.

Credit: swimlane.com
Frequently Asked Questions
What Are The Five Types Of Computer Security?
The five types of computer security are network security, information security, application security, operational security, and physical security. Network security protects against unauthorized access. Information security safeguards data. Application security prevents software vulnerabilities. Operational security involves policies and procedures. Physical security restricts access to hardware.
What Are The 5 Types Of Cyber Security?
The five types of cyber security are network security, application security, information security, operational security, and disaster recovery. Network security protects against unauthorized access. Application security safeguards software. Information security secures data integrity. Operational security manages processes. Disaster recovery ensures business continuity after breaches.
What Are The 5 Types Of Security?
The five types of security are network security, information security, physical security, operational security, and application security. Network security protects data during transfer. Information security safeguards data storage. Physical security prevents unauthorized access. Operational security manages processes and procedures. Application security secures software and apps from threats.
What Are The Four Types Of Security?
The four types of security include physical, network, application, and information security. Physical security protects hardware and facilities. Network security safeguards data during transmission. Application security ensures software safety. Information security protects data integrity and confidentiality.
Conclusion
Understanding computer security is essential for everyone today. It protects personal data. Shields businesses from threats. There are many types to consider. Antivirus software helps prevent malware attacks. Firewalls block unauthorized access. Encryption keeps data safe during transfer. Regular updates ensure systems stay secure.
Each type plays a unique role. Combining these strategies strengthens security. Always stay informed about new threats. With these tools, your digital world stays protected. Keep your devices and data safe. It’s crucial in our tech-driven lives.