Small businesses face cyber threats daily. Cybersecurity is crucial for protection.
A solid plan can safeguard your business from data breaches and online attacks. But, creating an effective cybersecurity plan can seem daunting. Where do you start? What should it include? These questions often puzzle small business owners who lack technical expertise.
Cybersecurity is not just for big companies. Small businesses are targets too. They often have fewer defenses, making them vulnerable. A well-crafted cybersecurity plan is your first line of defense. It helps you prepare and respond to threats efficiently. In this blog post, we will explore a practical example of a small business cybersecurity plan. This will guide you in creating a robust strategy to protect your business assets. Stay tuned to learn the essentials for safeguarding your digital space.
Credit: sectigostore.com
Introduction To Cyber Security
In today’s digital age, understanding cyber security is crucial for any business, especially small businesses. With increasing reliance on technology, protecting your business’s digital assets is not just a technical task—it’s a fundamental part of your business strategy. The stakes are high, and the threats are real. How prepared is your business?
Importance For Small Businesses
Small businesses often underestimate their risk of cyber threats. Yet, they are prime targets because they may lack robust security measures. Imagine losing your customer data or financial information to a hacker. The impact can be devastating.
Consider the financial implications of a breach. Not only might you face legal consequences, but you could also lose customer trust. Investing in cyber security can save you from these pitfalls.
It’s not just about installing antivirus software. It involves comprehensive planning, regular updates, and educating your staff. Have you considered how a breach could affect your business reputation?
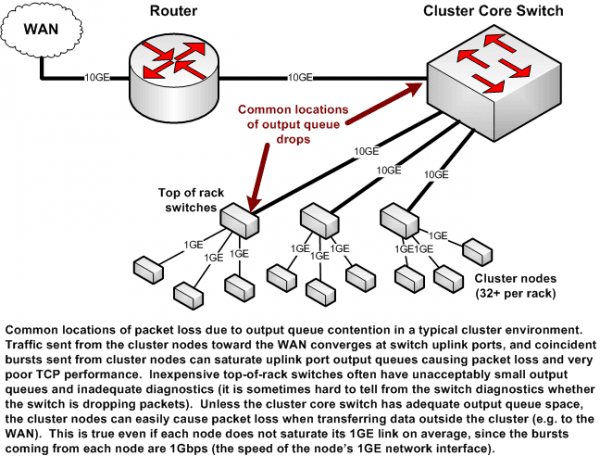
Common Threats Faced
Small businesses face a range of cyber threats daily. These can include phishing attacks, where an attacker tricks you into revealing sensitive information. Have you ever received an email that seemed legitimate but was actually a scam?
Ransomware is another common threat. This malicious software locks your files, demanding payment for their release. Think about the chaos of losing access to your business data.
Malware can infiltrate your systems without your knowledge, compromising data and slowing operations. How often do you scan your devices for malicious software? Regular checks are essential.
Each of these threats requires a proactive approach to cyber security. Are you taking the necessary steps to protect your business from these common dangers?
Credit: www.nsiserv.com
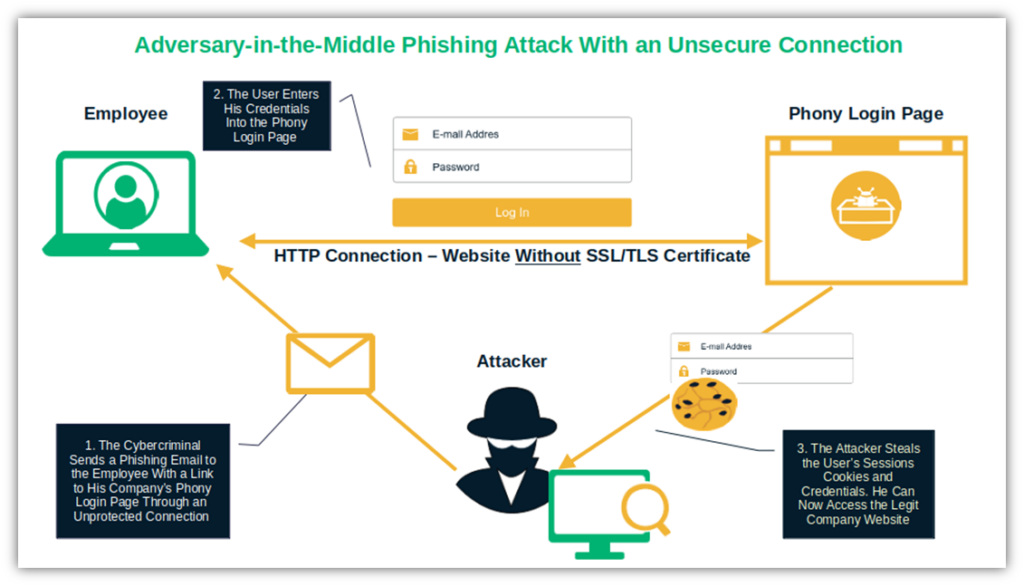
Assessing Vulnerabilities
Creating a robust cyber security plan for your small business starts with a crucial step: assessing vulnerabilities. Understanding where your business is at risk helps you protect sensitive information and maintain customer trust. By examining potential weak points, you can prioritize security measures that will have the most impact.
Identifying Weak Points
Every small business has unique vulnerabilities. Consider all entry points for digital threats, from outdated software to weak passwords. Imagine walking through your digital landscape—what areas seem unguarded? Identifying these weak points is the first step to fortifying your defenses.
Think about your previous experiences. Have you ever been locked out of an account because someone guessed your password? This simple oversight could be a vulnerability in your system. Pinpoint where similar gaps might exist in your business.
Tools For Vulnerability Assessment
Once you’ve identified potential weak points, leverage technology to assess them. Tools like Nessus, OpenVAS, and Qualys can scan your systems for vulnerabilities. These tools help you uncover risks that may not be immediately visible.
Consider using vulnerability assessment tools that fit your business size and budget. Many offer free versions with essential features for small businesses. They provide detailed reports, highlighting areas that require immediate attention.
Have you tested your system’s defenses lately? Regular assessments can reveal new vulnerabilities as your business grows and technology evolves. Make it a habit to use these tools regularly to stay ahead of potential threats.
Reflect on the last time you updated your software. Was it months ago? Keeping software up-to-date is a simple yet effective way to mitigate risks. It’s crucial for protecting your business from known vulnerabilities.
Think about how you can integrate these assessments into your routine. Will you set a monthly reminder? By consistently evaluating your vulnerabilities, you ensure a proactive approach to cyber security.
Creating A Security Policy
Building a security policy for a small business involves identifying risks and creating strategies to protect data. This plan includes employee training, regular system updates, and strong password policies. Clear guidelines help prevent cyber threats and ensure business continuity.
Creating a security policy is the cornerstone of safeguarding your small business from cyber threats. Imagine your business is a castle; a well-crafted security policy acts as the fortress walls, keeping intruders at bay. It’s more than just setting rules—it’s about creating a proactive defense strategy that evolves with the digital landscape. In today’s fast-paced world, cyber threats are continuously changing, and your security policy should be agile enough to adapt and protect your digital assets. Whether you’re a bakery, a tech startup, or a local bookstore, crafting a robust security policy can make a world of difference.Defining Security Goals
What does security mean for your business? This is the first question you should ask. Security goals are the objectives that guide your policy. They can be as simple as protecting customer data or as complex as ensuring compliance with industry regulations.Start by identifying what assets are most valuable. These could be customer information, proprietary technology, or financial records. Once you’ve pinpointed these, set clear goals to protect them.Consider the risks your business might face. Cyber threats vary greatly depending on the nature of your business. Tailor your security goals to address these specific risks effectively.Establishing Usage Guidelines
Usage guidelines are the rules that dictate how employees interact with company systems and data. Think of them as the manual that keeps everyone on the same page regarding security practices.Create guidelines that are easy to understand and follow. For instance, specify the types of passwords employees should use. Encourage strong, unique passwords and regular updates to minimize unauthorized access.Outline acceptable use of company devices and networks. This includes defining what can and cannot be done on work computers, ensuring they are used responsibly and securely.Provide training regularly. Cybersecurity is not just about rules; it’s about awareness. Equip your team with the knowledge they need to recognize potential threats and respond appropriately.How can you inspire your team to take security seriously? Share stories of businesses that suffered due to lax policies. These narratives can serve as powerful reminders of why security guidelines matter.Implementing Security Measures
Implementing security measures is crucial for protecting your small business from cyber threats. As technology advances, so do the tactics of cybercriminals. It’s essential to stay ahead by strengthening your defenses. This section will guide you through basic network security and data protection techniques to enhance your business’s security posture.
Network Security Basics
Start by securing your Wi-Fi network. Use a strong password and consider hiding the network name from public view. This simple step can deter unauthorized access.
Next, install a firewall. Think of it as a barrier between your internal network and external threats. It filters incoming and outgoing traffic based on security rules you set.
Regularly update your software and devices. Outdated systems are prone to vulnerabilities. Updates often include patches that fix security flaws.
Consider using a VPN. It encrypts data and hides your IP address, providing an extra layer of security, especially when accessing the internet from public locations.
Data Protection Techniques
Encrypt sensitive data. This means transforming it into a code that requires a key to access. Even if hackers get hold of your data, they can’t read it without the key.
Back up your data regularly. Use cloud storage or external hard drives. If your system is compromised, you won’t lose everything.
Limit access to sensitive information. Only allow employees who truly need it to view or modify it. This minimizes the risk of data leaks.
Implement strong password policies. Encourage employees to use complex passwords and change them frequently.
Train your staff. Make them aware of phishing scams and other tactics used by hackers. Knowledge is a powerful defense.
Are your current security measures enough to protect your business? Could a breach happen right under your nose without you realizing it? Taking these steps will help you fortify your small business against cyber threats. Remember, proactive measures are always better than reactive ones.
Employee Training
Small businesses need a solid cyber security plan to protect against threats. Employee training plays a vital role in ensuring safety. Regular sessions on identifying phishing scams and secure password practices help keep data secure and systems safe.
Employee training is a cornerstone of any effective small business cyber security plan. Employees are often the first line of defense against cyber threats. If they are not adequately trained, even the most robust security systems can be compromised.A well-structured training program empowers your team to recognize and respond to potential threats. It also fosters a culture of security awareness that benefits the entire organization.Developing Training Programs
Start by assessing your team’s current understanding of cyber security. What do they know? What are the gaps?Once you have a clear picture, develop a training program tailored to your business needs. Use engaging methods like workshops, webinars, or interactive sessions.Consider bringing in a cyber security expert to provide training. Their real-world insights can be invaluable. Make sure the training is ongoing, with regular updates to keep pace with evolving threats.Promoting Security Awareness
Security awareness should be woven into the fabric of your company culture. How can you make this happen?Encourage employees to share security tips and experiences. Create a forum for discussing cyber security challenges and solutions.Reward proactive security behavior. Recognizing employees who identify potential threats encourages others to be vigilant.Ask yourself: How can you keep security top of mind for your team? Regular reminders, newsletters, or quick quizzes can reinforce key concepts.Employee training is not a one-time event. It’s an ongoing commitment to keeping your business safe. How will you ensure your team is prepared for the next cyber threat?Incident Response Plan
Crafting a robust Incident Response Plan is crucial for small businesses. It helps identify and address cyber threats swiftly. By implementing clear steps, businesses can minimize damage and safeguard sensitive data effectively.
In today’s digital landscape, a robust Incident Response Plan is crucial for small businesses. It’s the blueprint that guides how you react when a cyber breach occurs, ensuring you can act swiftly to minimize damage. Think of it as your safety net, ready to catch you when the unexpected happens.Steps For Handling Breaches
When a breach strikes, speed is your best ally. First, identify the nature of the breach. Is it data theft, ransomware, or unauthorized access? Knowing what you’re dealing with helps you decide on the next steps.Contain the breach immediately to prevent further damage. For instance, if a computer is infected, disconnect it from the network. This simple action can stop the threat from spreading.Next, eradicate the threat. Remove malicious software and fix vulnerabilities. Make sure your systems are clean and safe before restoring any data.Finally, recover and restore operations. Ensure all systems are running smoothly and monitor them closely for any signs of recurring threats.Communication Strategies
Clear communication is key during a cyber incident. Who should you notify first? Your IT team, of course. They need to jump into action to mitigate the breach.Don’t forget about your employees. Inform them about the breach and any steps they need to take. This could be changing passwords or avoiding suspicious emails.What about your customers? If their data is compromised, they deserve to know. Transparency builds trust, even in tough times.Think about your external partners too. If they’re affected, they need the details to protect their own networks.Creating a detailed Incident Response Plan might seem daunting at first. But remember, it’s not just about protecting data; it’s about safeguarding your business’s reputation. Are you prepared to handle a breach when it happens?Regular Monitoring And Updates
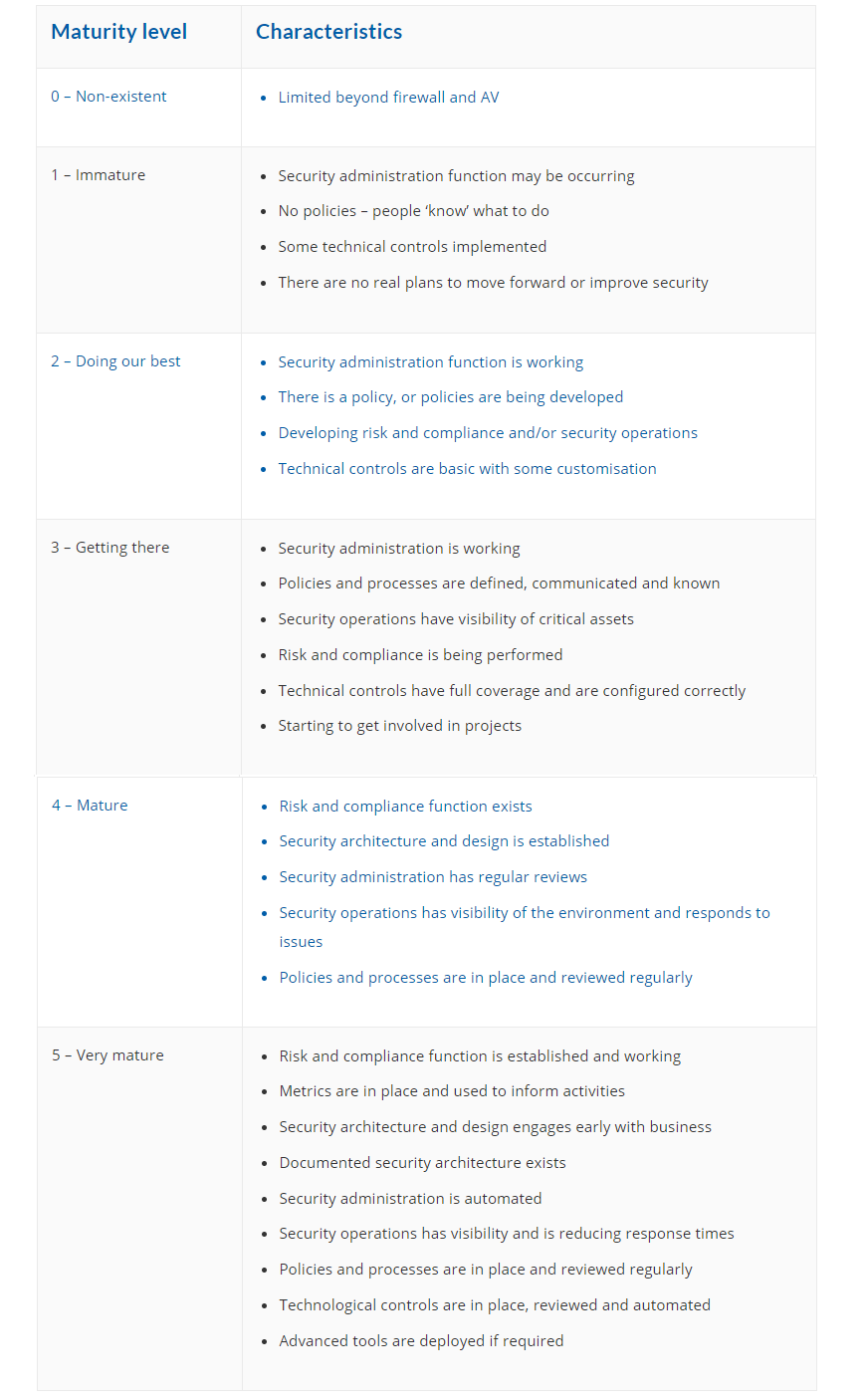
Maintaining a robust cyber security plan for your small business is not just about setting up initial defenses. It requires regular monitoring and updates to ensure your systems are always prepared to tackle new threats. Think of it as a routine check-up for your digital health. Just like you wouldn’t skip a doctor’s appointment, you shouldn’t ignore the importance of tracking and updating your security measures.
Tracking Security Performance
Have you ever wondered how effective your current security measures are? Regular tracking of security performance can answer this question. Utilize tools that provide real-time data on your security systems. This helps you identify weak spots before they become a problem.
Set up alerts for unusual activities. This proactive approach ensures you’re not caught off guard. Seeing a sudden spike in login attempts? That’s your cue to investigate further and tighten security.
Updating Systems And Policies
Updating your systems and policies is crucial in staying ahead of cyber threats. Technology evolves rapidly, and so do hacking techniques. Regular updates patch vulnerabilities and enhance protection.
Develop a schedule for updates. Consider monthly reviews of your security software and hardware. This keeps your defenses strong and resilient. Policies should evolve too, reflecting changes in technology and threat landscapes.
Are your employees aware of the latest security protocols? Regular training sessions can empower your team to recognize and respond to threats effectively. This ensures everyone is on the same page and your business remains secure.
How often do you revisit your cyber security plan? Regular updates and monitoring should be at the core of your strategy. This ensures you’re not just reacting to threats, but actively preventing them.

Credit: sectigostore.com
Evaluating And Improving
Creating a robust cyber security plan is crucial for small businesses. Regular evaluation and improvement are key to staying secure. It’s not enough to set up defenses once and forget about them. Technology and threats evolve rapidly. Businesses must adapt to protect sensitive data. Evaluating and improving your security measures ensures ongoing protection. This section covers crucial steps to enhance your cyber security.
Reviewing Security Effectiveness
Assess your current security measures regularly. Check for any weaknesses or outdated protocols. Use security audits and penetration tests to uncover vulnerabilities. These tests simulate attacks to see how your defenses hold up. Review logs and alerts for suspicious activities. Ensure that all software and systems are updated. This reduces the risk of exploitation from known vulnerabilities. Employee training is vital. Test their awareness with mock phishing exercises. Regularly update training materials to cover new threats.
Adapting To New Threats
Cyber threats change and evolve quickly. Stay informed about the latest attack methods. Follow security news and subscribe to threat intelligence feeds. Adapt your defenses to address new vulnerabilities. Implement advanced security technologies like AI for threat detection. Consider using managed security services for expert insights. Regularly update your risk assessment to address emerging threats. Ensure your incident response plan is flexible. Quickly adapt it to new threat scenarios. This helps minimize damage and recover faster.
Frequently Asked Questions
How Do I Write A Business Plan For Cyber Security?
To write a cybersecurity business plan, define your mission, goals, and target audience. Identify key services and competitors. Establish a marketing strategy and budget. Highlight team expertise and technology. Detail risk management and compliance measures. Ensure clarity and precision for effective communication.
What Are The 5 C’s Of Cyber Security?
The 5 C’s of cyber security are change, compliance, cost, continuity, and coverage. These principles ensure robust protection against threats. Effective implementation of these elements helps maintain system integrity, safeguard data, and streamline security management. Prioritizing these aspects is crucial for a resilient cyber security strategy.
How To Create A Cyber Security Plan?
Begin by assessing potential threats and vulnerabilities. Establish security policies and procedures. Implement strong access controls and regular software updates. Train employees on security awareness. Continuously monitor and review the plan for improvements.
Can You Make $500,000 A Year In Cyber Security?
Earning $500,000 annually in cybersecurity is possible with advanced skills and executive roles. Specialized fields like cybersecurity consulting and CISO positions offer lucrative salaries. Continuous learning and certifications can enhance career prospects. Networking and industry experience also play crucial roles in achieving high income in cybersecurity.
Conclusion
A strong cyber security plan protects your small business from threats. Regular updates are essential for security. Train your team to recognize risks. Monitor systems consistently to detect issues early. Back up important data to prevent loss. Use secure passwords and change them often.
Choose trusted software and tools. Implementing these steps reduces cyber risks. Stay informed on new security trends. Your business deserves robust protection. A good plan keeps your data safe. Invest time and effort in security. Your small business will thrive with a solid defense.