Cyber security protects our digital lives. It safeguards our data and privacy.
Its impact is vast and crucial for everyone connected online. As technology advances, threats evolve, posing new challenges. Cyber security is essential in safeguarding personal data, business secrets, and national security. In today’s digital world, cyber security is more important than ever.
It affects individuals, businesses, and governments alike. Hackers and cyber criminals constantly seek vulnerabilities, making robust security measures vital. Without strong protection, sensitive information can be stolen or misused. This can lead to financial loss, reputational damage, and privacy invasion. The impact of cyber security extends beyond technology—it influences trust, safety, and stability. Understanding its significance helps us navigate the digital landscape wisely. Stay informed and secure your online presence.
Cyber Security Importance
In today’s digital age, the importance of cyber security cannot be overstated. With our lives increasingly intertwined with technology, safeguarding your digital assets has become paramount. From protecting your personal data to ensuring business continuity, cyber security plays a crucial role in maintaining trust and stability in our digital environment.
Protecting Personal Data
Your personal data is like your digital fingerprint. It’s unique, sensitive, and deserving of robust protection. Consider the amount of personal information you share online: banking details, photos, or even your location. This data can be easily exploited if not properly secured.
Imagine waking up to find your bank account drained or your identity stolen. Scary, right? Securing your personal data is not just about using strong passwords; it’s about being aware of phishing scams and securing your devices with the latest updates.
Ask yourself: Are you doing enough to protect your personal data? Regularly updating your software and being cautious about sharing information can make a significant difference.
Ensuring Business Continuity
Cyber threats can disrupt a business overnight, leading to financial loss and damaged reputation. For businesses, cyber security is not just a safety measure; it’s a necessity for survival.
Picture this: A small business owner wakes up to find their website hacked and customer data compromised. This can lead to a loss of customer trust and potential legal consequences. Implementing a strong cyber security strategy ensures your business can continue operating smoothly even when faced with cyber threats.
Have you considered how a cyber attack could impact your business? Regular audits, employee training, and a robust security infrastructure can help you stay resilient and protect your business interests.
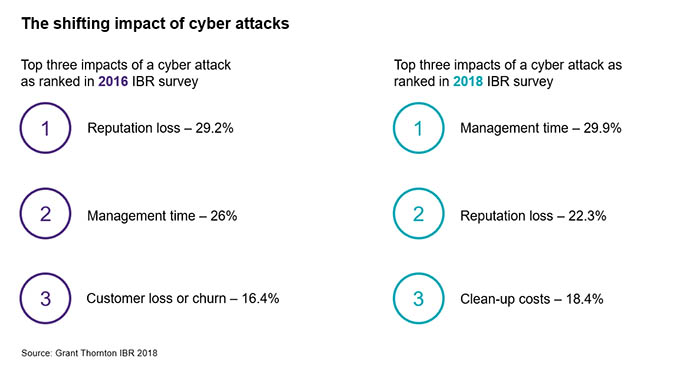
Credit: www.grantthornton.global
Current Threat Landscape
Understanding the current threat landscape in cyber security is crucial for anyone navigating the digital world. With the rapid evolution of technology, cyber threats are becoming more sophisticated and frequent. You might think that only large corporations are targeted, but individuals are equally at risk. It’s essential to stay informed about the prevalent threats, which include ransomware attacks and phishing scams. Let’s delve into these threats and see how they impact your online safety.
Ransomware Attacks
Ransomware attacks have surged in recent years, affecting both businesses and individuals. Imagine waking up to find your computer locked, with all your files inaccessible. This is the reality of ransomware, where attackers demand a ransom to restore access. It’s like having your digital life held hostage.
These attacks often start with innocent-looking email attachments or downloads. Once activated, they can spread quickly across networks, encrypting files and causing chaos. Consider backing up your data regularly and keeping your software updated. These simple actions can be your first line of defense.
Have you ever thought about how much you rely on your digital devices? Losing access to them can be devastating. Don’t wait for it to happen to you before you take action. Protect your digital world proactively.
Phishing Scams
Phishing scams are another prevalent threat in today’s cyber landscape. These scams trick you into revealing personal information, like passwords and credit card details. They often disguise themselves as trustworthy sources, like your bank or a favorite shopping site.
Think about the last time you received an email asking for urgent action. Did you hesitate or click without thinking? Phishing relies on urgency and fear. It’s important to scrutinize emails and verify their authenticity before responding.
Consider using strong passwords and enabling two-factor authentication. These steps can make it harder for phishers to succeed. How vigilant are you when checking your emails? Being cautious can save you from falling victim to these scams.
Emerging Technologies
Emerging technologies shape the landscape of cyber security. They redefine how we protect data and systems. Companies must adapt to these changes to stay secure. Two key technologies are AI and machine learning, and blockchain applications. Each offers unique benefits and challenges. Understanding them is vital for future security strategies.
Ai And Machine Learning
AI can identify threats quickly. It analyzes vast amounts of data efficiently. Machine learning helps systems learn from past attacks. This creates smarter security solutions. It also reduces human error. Automated responses can prevent breaches. Yet, AI systems need constant updates. They must evolve as threats evolve.
Blockchain Applications
Blockchain secures transactions with encryption. It offers transparency and trust. Each transaction is verified. This reduces fraud risks. Blockchain can protect sensitive information. It ensures data integrity. Yet, it requires careful implementation. Poorly designed systems can be vulnerable.

Credit: www.impactmybiz.com
Role Of Governments
As cyber threats evolve, the role of governments in safeguarding cyberspace becomes increasingly crucial. Governments have the power to create and enforce policies that protect individuals and organizations from cyber-attacks. But what exactly are they doing to make the digital world safer for you?
Regulatory Frameworks
Governments worldwide are establishing regulatory frameworks to combat cybercrime. These frameworks set standards for data protection and cybersecurity practices. For example, the General Data Protection Regulation (GDPR) in Europe has transformed how businesses handle personal data. It’s not just about compliance; it’s about ensuring your data is safe.
Regulatory frameworks also encourage transparency. When companies report data breaches, governments can act swiftly to mitigate risks. You gain a sense of security knowing there’s oversight. But are these regulations enough to deter sophisticated cyber threats?
International Cooperation
Cybersecurity is not limited by borders. Governments are increasingly engaging in international cooperation to tackle global cyber threats. They share intelligence, resources, and strategies to build a united front against hackers. Think of it as a global neighborhood watch, working together to keep your digital environment secure.
International cooperation also helps standardize cybersecurity norms. When nations agree on common policies, it reduces the loopholes that cybercriminals exploit. But can such cooperation address every potential threat? You might wonder how effective these alliances truly are.
Governments play a pivotal role in shaping the cybersecurity landscape. Their actions directly impact how safe you feel online. As you navigate the digital world, consider how these regulatory measures and international collaborations affect your daily interactions. Are they doing enough, or is there room for improvement?
Corporate Responsibility
Corporate responsibility in cyber security has grown in importance. Businesses must protect sensitive data. They should also ensure safe digital environments. This responsibility goes beyond compliance. It involves creating a secure culture within the organization. Companies need to take proactive steps. This ensures they stay ahead of cyber threats.
Employee Training Programs
Effective employee training programs are vital. They educate staff about cyber threats. Employees learn to identify phishing attempts. They also understand secure password practices. Regular training updates are necessary. Cyber threats evolve quickly. Staff must stay informed. Engaging training methods improve retention. Interactive sessions and real-life scenarios work well. This empowers employees to act securely.
Incident Response Plans
Incident response plans prepare companies for cyber attacks. They define steps to take after a breach. Quick response minimizes damage. These plans assign roles to team members. Everyone knows their responsibilities. Regular drills test the plan’s effectiveness. Updates to the plan should follow new threats. This ensures it remains relevant. A well-prepared team responds efficiently. This reduces downtime and protects data.
Cyber Security Tools
Cyber security tools are essential for protecting digital assets. They help guard against cyber threats and data breaches. These tools include various types of software and hardware. Each serves a specific function to enhance security. Let’s explore two key tools: antivirus software and firewalls.
Antivirus Software
Antivirus software detects and removes malicious programs. It scans files and systems for viruses and malware. This software updates regularly to tackle new threats. It acts as a first line of defense for your computer. Without it, your data is at risk.
Firewalls
Firewalls control incoming and outgoing network traffic. They act as barriers between trusted and untrusted networks. A firewall monitors data and blocks suspicious activity. It helps prevent unauthorized access to your systems. Firewalls can be hardware, software, or a combination of both.
Future Challenges
Cybersecurity faces evolving threats with technology advancing rapidly. Protecting sensitive data becomes crucial against sophisticated cyber attacks. Organizations must adapt to safeguard their digital assets effectively.
In the rapidly evolving world of technology, cyber security faces new challenges daily. Understanding future challenges helps prepare for threats. As technology advances, so do the tactics of cybercriminals. Two areas of concern are Quantum Computing and IoT Vulnerabilities. These pose significant risks to our digital security. Let’s explore these challenges further.Quantum Computing Risks
Quantum computing can break current encryption methods. This poses a threat to data privacy. Traditional encryption methods may become useless. Cybercriminals can access sensitive information easily. Businesses and governments must prepare. New encryption techniques are needed to combat this threat. This ensures data remains safe in a quantum world.Iot Vulnerabilities
The Internet of Things connects devices worldwide. This increases the risk of cyber attacks. Many IoT devices lack strong security measures. Hackers can exploit these weak points. Devices like smart cameras and thermostats are at risk. Users must ensure devices have the latest security updates. Strong passwords and regular updates can help protect IoT devices.Individual Best Practices
Cyber security affects everyone. Personal safety online is vital. Simple actions can protect us. These steps help guard our information. Let’s explore some effective practices.
Password Management
Strong passwords are essential. Avoid simple words or sequences. Use a mix of letters, numbers, and symbols. Change passwords regularly. Consider using a password manager. These tools store and encrypt your passwords. They make it easier to maintain unique passwords for each account.
Safe Browsing Habits
Be cautious online. Avoid clicking unknown links. They might lead to harmful sites. Always check a website’s URL. Secure sites start with “https”. Look for a padlock symbol in the address bar. It shows the site is secure. Use a reliable antivirus program. It helps block dangerous sites and downloads.

Credit: www.helpnetsecurity.com
Frequently Asked Questions
What Is Impact In Cyber Security?
Impact in cybersecurity refers to the consequences of security breaches. It includes data loss, financial damage, and reputational harm. Businesses can face legal penalties and operational disruptions. Effective cybersecurity measures help mitigate these impacts, ensuring data protection and business continuity.
What Is The Impact Of Cyber Security?
Cyber security protects sensitive data, prevents unauthorized access, and ensures smooth digital operations. It safeguards businesses from financial losses, reputational damage, and legal issues. Effective cyber security measures enhance customer trust and compliance with regulations, supporting overall organizational growth and stability.
What Is Cyber Security Impact Level?
Cyber security impact level assesses the potential damage from a cyber threat. It categorizes risk from low to high, guiding security measures.
What Is Impact Of Security?
Security impacts business reputation, customer trust, and data protection. Strong security measures prevent breaches and financial losses. Enhanced security boosts consumer confidence, leading to increased sales and growth. Poor security risks data leaks, damaging brand credibility and customer relations. Implementing effective security safeguards is crucial for business success and longevity.
Conclusion
Cybersecurity shapes our digital future. Protects data and privacy. It’s vital. Threats grow daily. Solutions must evolve rapidly. Businesses should prioritize security strategies. Individuals need awareness too. Educate yourself on cyber threats. Use strong passwords. Update software regularly. Stay vigilant online.
Cybersecurity impacts everyone. Safeguard your digital life today. Simple steps make a big difference. Protect yourself and others. The digital world requires constant vigilance. Embrace security measures. They are necessary. Prevent cyber attacks. Stay secure. Be proactive, not reactive. Cybersecurity is everyone’s responsibility.
Make it a priority. Keep your data safe. Stay informed. Stay secure.










