Cyber threats are on the rise. Businesses need strong protection.
A Cybersecurity Risk Management Plan is essential for safeguarding digital assets. This plan helps identify, analyze, and respond to threats. It ensures that sensitive data stays secure. Cybersecurity involves more than just firewalls or antivirus software. It requires a strategic approach, tailored to each organization’s needs.
This plan guides companies in understanding their vulnerabilities. It also helps them prioritize actions to mitigate risks. With cyber attacks becoming more sophisticated, businesses must stay vigilant. A comprehensive plan not only protects assets but also boosts trust among customers and stakeholders. Dive into how creating a solid Cybersecurity Risk Management Plan can help you navigate the complex landscape of digital security.
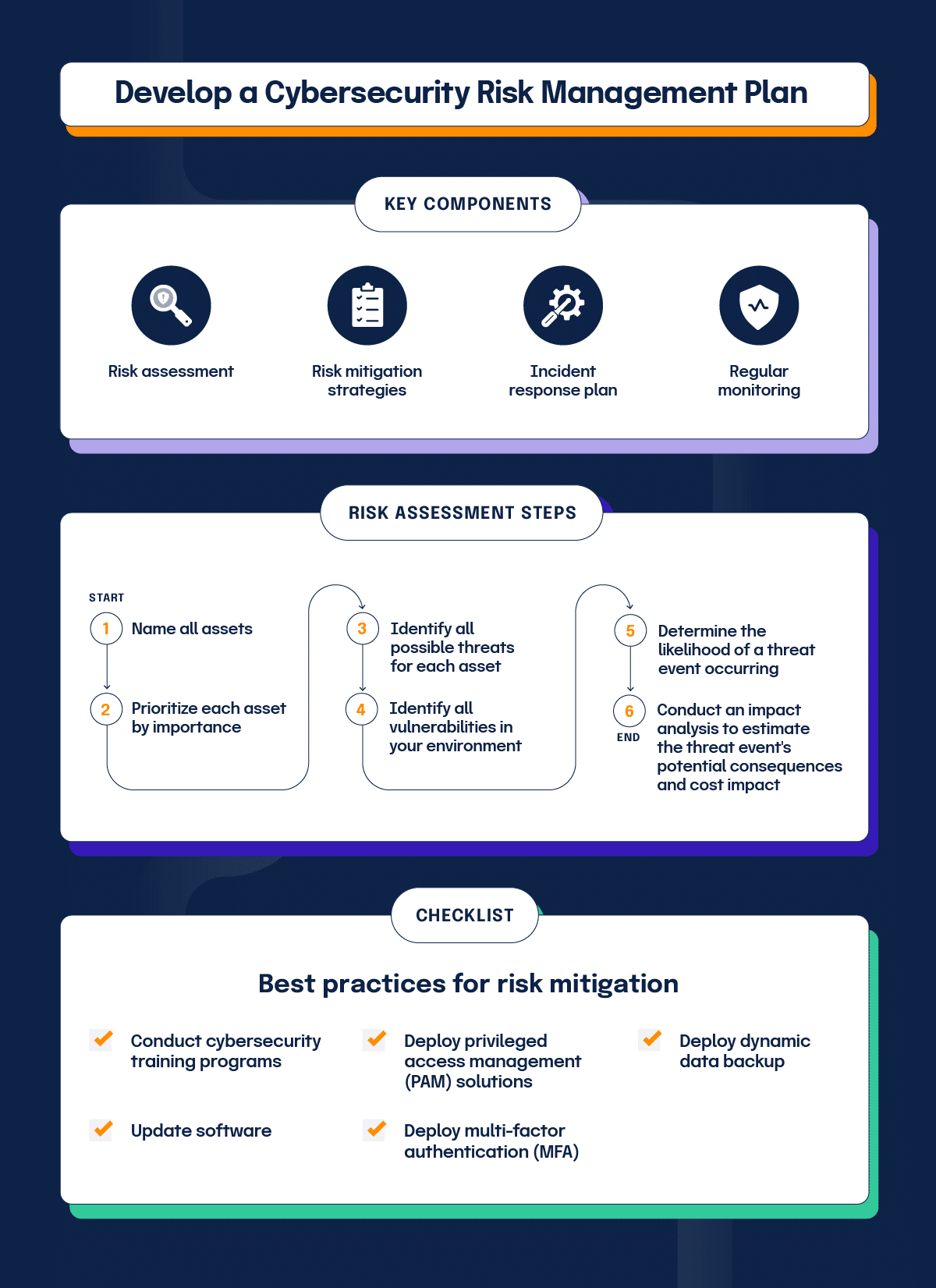
Credit: hyperproof.io
Identifying Cyber Threats
Understanding cyber threats is vital for any cybersecurity risk management plan. These threats evolve constantly, challenging businesses to stay vigilant. Identifying them early can prevent severe damage. Recognizing common and emerging threats helps in crafting a robust defense strategy.
Common Cyber Threats
Phishing attacks deceive users into revealing sensitive information. Cybercriminals use emails that look genuine. Malware infiltrates systems through infected software or files. It can steal data or disrupt operations. Ransomware locks access to data until a ransom is paid. This threat can cripple businesses.
Denial-of-Service attacks flood systems with traffic. They aim to disrupt service availability. Insider threats involve staff misusing access rights. They might leak confidential information. These threats often go unnoticed until damage occurs.
Emerging Threats
Artificial Intelligence enhances cyber attacks. Hackers use AI for automated targeting. Deepfakes create realistic fake media content. They can spread misinformation easily. Quantum computing poses risks to encryption methods. It can break complex codes faster.
Internet of Things devices are vulnerable. They often lack proper security measures. Cybercriminals exploit these weaknesses. Cloud security issues arise with data storage changes. Unauthorized access and breaches become more likely.
Understanding these threats is crucial. It allows businesses to prepare effectively. Stay informed about new risks. Adapt your strategies to ensure safety.
Assessing Vulnerabilities
Identifying weaknesses is crucial in a cybersecurity risk management plan. Regular assessments help uncover vulnerabilities and strengthen defenses. Prioritizing risks ensures effective resource allocation and better protection against potential threats.
Assessing vulnerabilities is a critical step in crafting a robust cybersecurity risk management plan. It involves identifying potential weaknesses in your system that hackers might exploit. By understanding where these vulnerabilities lie, you can better protect your digital assets and maintain your organization’s integrity. Let’s dive into two main areas where vulnerabilities often occur: networks and applications.Network Vulnerabilities
Your network is the backbone of your organization’s IT infrastructure. A single weak spot can open the door to cyber threats. Consider the security of your Wi-Fi networks. Are they password protected and encrypted? Ensure you regularly update your router’s firmware to patch any known vulnerabilities.Firewalls are another key component. They act as a barrier between your internal network and external threats. Are your firewall settings optimized? Regularly review and adjust your firewall rules to block unauthorized access.Pay attention to your network segmentation. Is your network divided into segments to limit access and control traffic? Proper segmentation can prevent a breach in one area from spreading throughout your entire network.Application Vulnerabilities
Applications are often the target of cyber attacks due to their complexity and widespread use. Examine the software you use daily. Is it up to date? Outdated software often contains vulnerabilities that hackers can exploit.Focus on user authentication processes. Are your applications using strong, multi-factor authentication? This adds an extra layer of security, making it harder for unauthorized users to gain access.Think about the data your applications handle. Is sensitive information encrypted? Encrypting data both in transit and at rest can protect it from unauthorized access.Take the time to conduct regular security assessments. How often do you perform vulnerability scans on your applications? Frequent scanning can help identify new vulnerabilities before they become serious threats.By carefully assessing these vulnerabilities, you can strengthen your cybersecurity posture and safeguard your organization’s valuable information. What steps will you take today to address potential weaknesses in your systems?Risk Analysis Techniques
Cybersecurity risk management plans utilize diverse techniques to identify potential threats and vulnerabilities. Effective analysis includes evaluating risks, prioritizing assets, and implementing safeguards. These strategies help organizations protect sensitive information and maintain robust security systems.
Risk analysis techniques are vital in cybersecurity. They help identify threats. Understanding these techniques strengthens a cybersecurity risk management plan. Organizations must assess potential risks. This ensures protection against cyber threats.Quantitative Risk Analysis
Quantitative risk analysis deals with numbers. It calculates the probability of a threat. It measures the potential impact in monetary terms. This method uses data and statistics. It helps prioritize risks based on financial loss. It provides a clear view of potential damage. Decision-makers can allocate resources effectively. They focus on high-risk areas first.Qualitative Risk Analysis
Qualitative risk analysis is subjective. It assesses risks using descriptions. Experts evaluate the severity of threats. They use experience and judgment. This method categorizes risks as high, medium, or low. It relies on opinions rather than numbers. It helps understand the nature of threats. This approach is useful where data is scarce. Teams can communicate risks more easily. It aids in developing strategic responses.Developing Security Policies
Developing effective security policies is crucial for a robust cybersecurity plan. These policies provide clear guidance on protecting digital assets. They help prevent unauthorized access and ensure data integrity. Well-defined policies align business goals with security measures. They also set expectations for employees and stakeholders. Creating these policies involves understanding risks and prioritizing actions.
Policy Frameworks
Security policy frameworks form the backbone of a cybersecurity strategy. They offer structured guidelines for securing information and systems. Frameworks like ISO 27001 and NIST Cybersecurity Framework are widely recognized. They provide comprehensive methodologies for managing security risks. Adopting these frameworks ensures consistency and reliability in security practices. Organizations benefit from proven strategies and international standards. This helps maintain a strong defense against cyber threats.
Compliance Considerations
Compliance with legal and regulatory requirements is vital. Security policies must adhere to laws like GDPR and HIPAA. These laws protect sensitive data and personal information. Non-compliance can lead to severe penalties and reputational damage. Policies should address specific compliance needs for different industries. This ensures all legal obligations are met efficiently. Regular audits and assessments help maintain compliance standards. They identify gaps and areas needing improvement.
Implementing Security Controls
Security controls are vital in a Cybersecurity Risk Management Plan. They help protect data from unauthorized access and breaches. Implementing these measures reduces vulnerabilities and strengthens overall system security.
Implementing security controls is a critical step in any cybersecurity risk management plan. This process involves putting in place measures to protect your data and systems from potential threats. Whether you’re a small business owner or part of a large corporation, understanding how to effectively implement these controls can make a significant difference in your cybersecurity posture.Technical Controls
Technical controls are the tools and technologies you use to protect your systems. These include firewalls, antivirus software, and encryption. They act as your first line of defense against cyber threats.Regular updates to software and systems are crucial. Outdated technology can be an easy target for hackers. By keeping your tools current, you reduce the risk of vulnerabilities.Consider the story of a small business owner who ignored software updates. They experienced a data breach that could have been avoided. This highlights the importance of proactive technical measures.Administrative Controls
Administrative controls focus on the policies and procedures that guide your cybersecurity practices. They ensure everyone in the organization knows their role in protecting data. These controls include training, security policies, and access management.Training employees regularly is vital. Many breaches occur due to human error. Educating your team on recognizing phishing emails can significantly reduce this risk.Imagine you receive a suspicious email. If you’ve been trained, you’ll know to report it rather than clicking any links. This simple action can prevent a potential threat from escalating.Implementing these security controls requires commitment and consistency. How often do you review and update your cybersecurity measures? Making this a regular practice can protect your business from costly breaches.By taking these practical steps, you’re actively safeguarding your organization’s future.
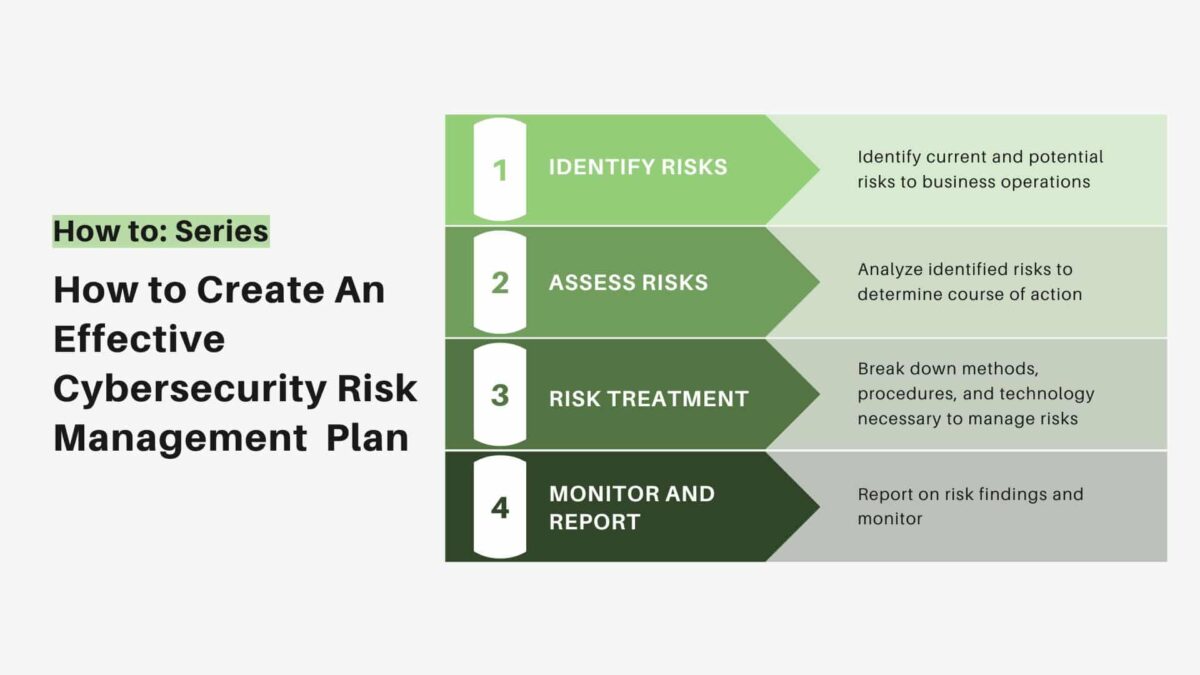
Credit: www.titanfile.com
Monitoring And Detection
In today’s digital age, protecting data is essential. A cybersecurity risk management plan is vital for businesses. Monitoring and detection are key components of this plan. They help identify and address threats quickly. Continuous monitoring keeps systems secure and operational.
Real-time Monitoring
Real-time monitoring provides immediate insights into network activity. It tracks data flow and system usage constantly. This constant vigilance helps spot unusual patterns. Immediate alerts can prevent potential breaches. With real-time insights, businesses stay ahead of threats. It boosts confidence in system security. It minimizes downtime and data loss.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) are crucial tools. They identify unauthorized access attempts. IDS monitors network traffic for suspicious activities. It alerts security teams of potential breaches. There are two main types of IDS: Network-based and Host-based.
Network-based IDS examines data traveling across the entire network. Host-based IDS focuses on individual devices. Both types work together for comprehensive protection. Implementing IDS helps maintain a secure environment. It ensures sensitive information remains safe.
Incident Response Planning
Incident response planning is crucial for any cybersecurity risk management plan. When a cyber attack strikes, you need a clear strategy to mitigate damage and restore normalcy. It’s not just about having a plan; it’s about having the right plan tailored to your organization’s needs. This involves assembling the right team and developing solid recovery strategies. Let’s explore how you can effectively build your incident response plan.
Building Response Teams
Imagine your computer network under siege—what’s your first move? You need a well-trained response team ready to act. These teams should include IT professionals, legal advisors, and communication experts. Each member plays a vital role in handling different aspects of a cyber incident.
Having diverse skills within your team ensures that you cover all bases. IT experts can tackle technical issues while communication specialists manage public relations. Legal advisors can help navigate regulatory challenges. This balanced approach is essential for a swift and comprehensive response.
Have you considered cross-training your team members? It might be a good idea. This ensures that everyone can step in if a primary team member is unavailable. Regular drills and simulations can also prepare your team for real-world scenarios. Are your team members ready for action?
Recovery Strategies
Once the threat is contained, how do you get back to business? Recovery strategies should focus on restoring data and services as quickly as possible. Backup systems play a critical role here. Ensure your backups are frequent, secure, and easily accessible.
Consider implementing cloud solutions for data recovery. They offer flexibility and speed that traditional methods might lack. But remember, recovery isn’t just about technology—it’s about your people too. Support your staff emotionally and professionally as they navigate the aftermath of a cyber incident.
What if your recovery plan falls short? Learn from each incident. Analyze what worked and what didn’t, then adjust your strategy accordingly. Continuous improvement is the key to resilience. Are you ready to refine your plan for a stronger future?
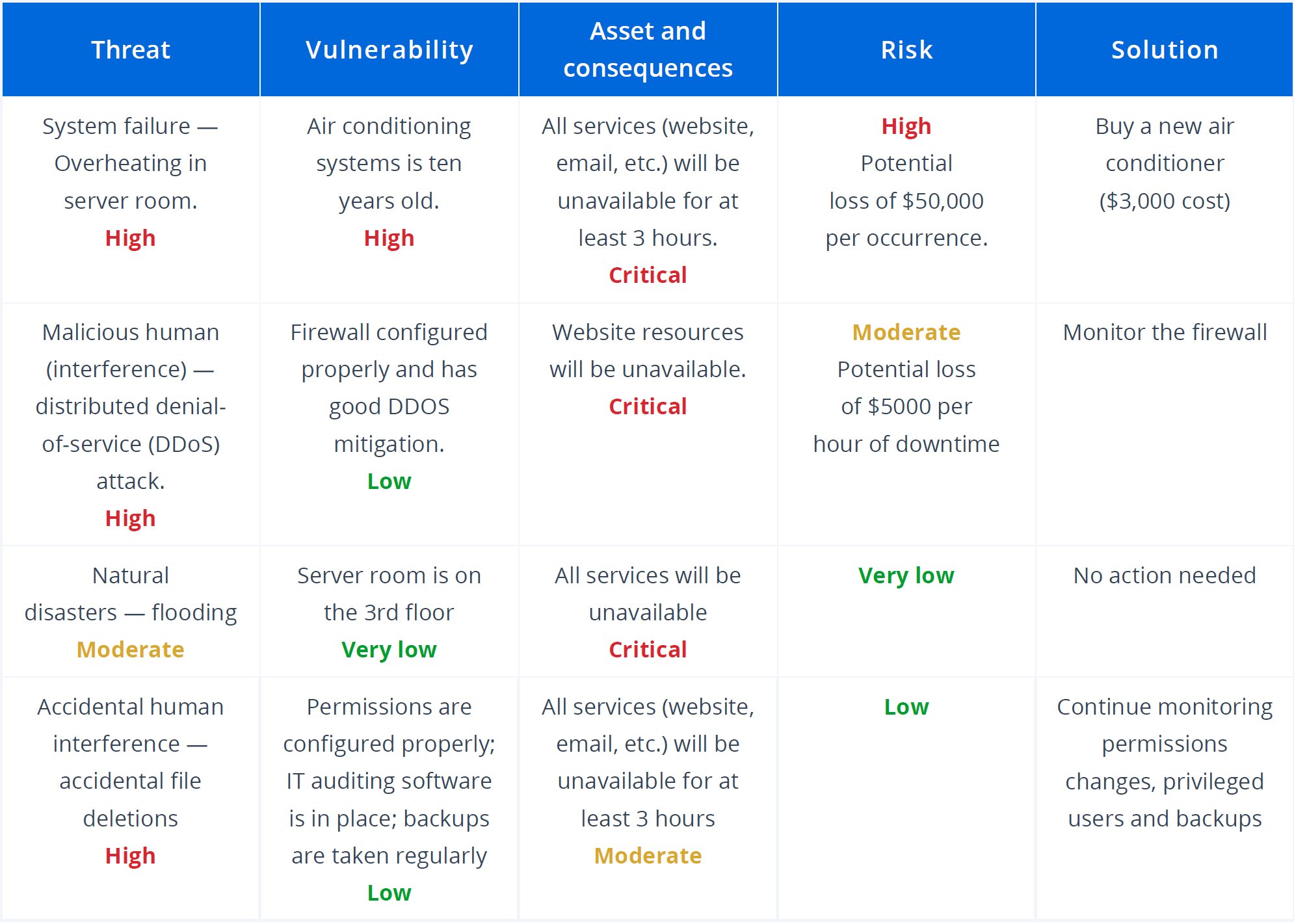
Credit: www.netwrix.com
Continuous Improvement
Enhancing cybersecurity risk management involves continuous improvement. Regular updates ensure defenses remain effective against evolving threats. Assessing vulnerabilities and refining strategies leads to a stronger security posture.
Continuous improvement in cybersecurity risk management is vital for keeping your defenses robust and adaptive. Technology evolves rapidly, and threats can emerge from unexpected corners. By regularly assessing and updating your security measures, you ensure your organization stays a step ahead of cybercriminals.###Regular Audits
Regular audits are the backbone of a strong cybersecurity risk management plan. They help identify vulnerabilities that could be exploited by attackers.Consider scheduling these audits quarterly or bi-annually. This frequency allows you to catch issues before they become major problems. During an audit, assess all systems, applications, and networks for weak spots.Think of audits as a health check-up for your digital infrastructure. You wouldn’t ignore a doctor’s advice after a health exam, right? Similarly, act promptly on audit findings to strengthen your defenses.###Updating Security Measures
Updating security measures is not just about installing the latest software patch. It involves a holistic approach to safeguarding your assets.Ask yourself: Are your firewalls updated? Is your antivirus software current? Outdated systems are a playground for hackers.Engage your IT team to review and refine security protocols regularly. Encourage them to stay informed about the latest threats and countermeasures.Remember the last time you updated your phone’s operating system? It wasn’t just about new features; it also closed security loopholes. Apply this mindset to your cybersecurity strategy.Continuous improvement is an ongoing journey. With regular audits and updated security measures, your cybersecurity plan can adapt to new challenges. Are you ready to make these practices a regular part of your routine?Frequently Asked Questions
What Are The 5 Risk Management Plan?
The five risk management plans are: Identify risks, assess risks, prioritize risks, implement risk responses, and monitor risks. These steps help organizations manage potential threats effectively, ensuring minimal impact on operations and goals. Developing a solid risk management strategy is crucial for long-term success and resilience.
What Is A Security Risk Management Plan?
A security risk management plan identifies, assesses, and mitigates potential security threats. It helps protect assets and data. This plan includes strategies for risk prevention and response. Regular updates ensure it addresses evolving security challenges. Businesses use it to minimize risks and ensure operational continuity.
What Is A Cybersecurity Risk Management Plan?
A cybersecurity risk management plan identifies, assesses, and mitigates security risks to protect an organization’s data. It involves continuous monitoring, implementing security measures, and ensuring compliance with regulations. The goal is to minimize potential threats and vulnerabilities, safeguarding critical information and assets.
What Is Risk Management In Cyber Security?
Risk management in cyber security involves identifying, assessing, and mitigating threats to digital assets. It prioritizes protecting data, systems, and networks. Effective strategies include regular assessments, implementing security controls, and ensuring compliance with regulations. Proactive planning helps minimize potential damages from cyber attacks and enhances overall security posture.
Conclusion
Creating a cybersecurity risk management plan is essential. Protects sensitive data. Prevents breaches. Keeps your business secure. A clear plan builds trust. Employees feel safe. Customers appreciate it. Regular updates ensure effectiveness. Adapt to new threats. Stay ahead. Invest time in training.
Educate your team. Everyone plays a role. Cyber threats evolve. Stay informed. Review your plan often. Make adjustments. Security is a continuous journey. Maintain vigilance. Your business depends on it. A proactive approach protects assets. Safeguards reputation. Peace of mind for everyone involved.